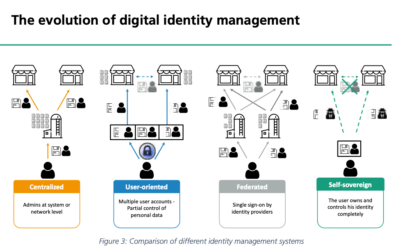
The challenge is that the confirmation of who is on the phone (proof of identity) needs to happen both ways, not just one way.
From the Blog on digital identity
Aid Agencies, Credit Cards, and Data Governance
How could we, as aid agencies, learn from the credit card data governance model? Not pure adoption, but learn from it.
What if we called it a ‘profile’?
In the humanitarian space, identity leads us into discussions we don’t need and usually don’t want. what if we just called it a profile?
The Registration Function
What would happen if we implemented good practice from other areas? What if those doing registration were not implementing?
Maybe we don’t need to control everything
A government issues a passport – they register, verify, prove uniqueness, and maintain the list. They do can’t control how it is used.
Looking Back
There are great people doing amazing things out there. Check out what inspired us this week, What inspired you this week?
The Power of Yes/No
Yes/No can help us with inclusion, exclusion and duplication without actually sharing the information. We do this already and we can improve.
I wish you would have asked me first
Our contact details are shared without our knowledge by organisations and companies often with profit (for them) intention. Perhaps we should ask first?
Data Portability won’t work on its own
I remain an advocate for data portability, but it is not the magic bullet. It risks the ‘Six of one, half a dozen of another’ trap.